DIY LAN Turtle - Building a Stealth Remote Access Device
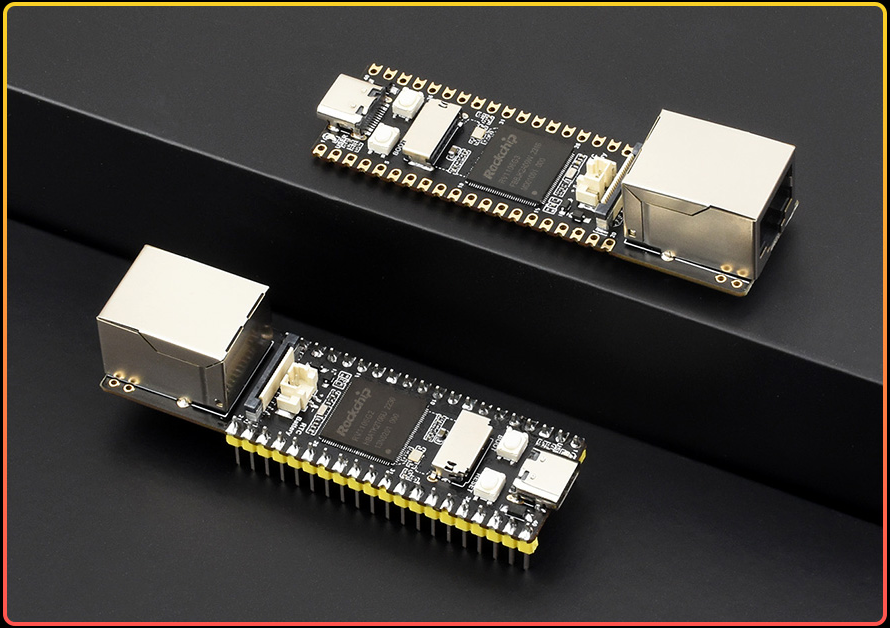
In this post, I share my experience building a DIY stealth remote access device using the Luckfox Pico Max RV1106. Inspired by the commercial LAN Turtle but seeking a more affordable solution, I created this device to enable remote network access without complex port forwarding or traditional VPN setups. This project served as both a practical solution and a valuable learning experience in hardware integration and network security.
⚠️ WARNING ⚠️
This project uses free third-party services! And as the saying goes: if it's free, you are the product! This is just an example of usage. My goal is not to connect to locations that could compromise sensitive information or infrastructure.
Idea
My goal was simple: I wanted reliable remote access to local networks without the hassle of complex VPN setups or router configuration. Since I often don’t have access to the router, I needed a true plug-and-play solution. While the commercial LAN Turtle provides these capabilities, its high price pushed me to explore a more cost-effective alternative. This project became an opportunity not just to build my own solution, but also to gain a deeper understanding of the underlying technologies.

Hardware Selection
After researching various options, I chose the Luckfox Pico Max RV1106 as the core of my project. This compact device offers an impressive set of features at a remarkably affordable price point.

Specifications
| Component | Details |
|---|---|
| Processor | Cortex A7 @ 1.2GHz |
| NPU | Max: 1 TOPS, supports int4, int8, and int16 |
| ISP | Input 5M @30fps (Max) |
| Memory | Max: 256MB DDR2 |
| USB | USB 2.0 Host/Device |
| Camera | MIPI CSI 2-lane |
| GPIO | 26 × GPIO pins |
| Ethernet Port | 10/100M Ethernet controller and embedded PHY |
| Default Storage | SPI NAND FLASH (256MB) |
While it lacks some features I would have liked (PoE and Gigabit Ethernet), the price-to-performance ratio made it an excellent choice for my project.
Alternative Hardware Options
For those interested in trying different hardware, here are some alternatives I considered:
- Raspberry Pi Zero W + USB Ethernet
- Orange Pi Zero 3
- GL.iNet GL-MT300N V2
- ESP32-S3 ¿¿Maybe??
- M5Stack LLM630
🛍️ Shopping List & Cost Analysis
Here’s what I used for this project:
- Luckfox Pico Max RV1106 - €18
- 64GB microSD card - €10
- microSD to USB adapter - €2
- Total: €30
Cost Comparison:
- Commercial LAN Turtle: ~€200-300
- DIY Solution: €30
- Savings: ~85-90%
Optional Additions:
- 3D printed case: €2-5 (filament cost)
- Power bank (portable use): €15-25
- USB-C to Ethernet adapter: €10-15

� Smecurity & Legal Considerations
Important: This device should only be used on networks you own or have explicit permission to access. Unauthorized network access is illegal in most jurisdictions.
Security Best Practices:
- Change default passwords immediately after setup
- Enable SSH key authentication and disable password login
- Regularly update the system:
sudo apt update && sudo apt upgrade - Monitor device access logs:
sudo journalctl -f - Use strong API tokens and rotate them regularly
- Consider using a dedicated VLAN for the device
Privacy Considerations:
- Third-party VPN services can potentially log your traffic
- Consider self-hosted alternatives like WireGuard for sensitive environments
- Review the privacy policy of your chosen VPN provider
🚀 Implementation Luckfox Pico
I performed all testing on Linux. Here’s how I put everything together:
Setting Up the SDK
First, I prepared my development environment:
|
|
|
|
In the lunch script, I selected:
- RV1106 board [6]
- SD Card boot [0]
- Ubuntu OS [1]
Building the Operating System
After several attempts, I discovered that the third-party VPN required the UTS namespace to be enabled in the kernel. Here’s how I activated it:
|
|
I navigated to:
|
|
After saving the configuration and building the kernel, the output files were stored in luckfox-pico/output/image/.
Luckfox Pico OS Installation
For installation, I used a Windows VM and the SocToolKit software from the SDK (luckfox-pico/tools/windows/SocToolKit). The process was straightforward - just selecting the compiled image files and target microSD card. The official documentation provides detailed instructions if needed.
Network Configuration
After the OS installation, I needed to configure the eth0 interface for DHCP. This ensures the device automatically gets an IP address when connected to a network:
|
|
Add the following configuration:
|
|
To apply the changes without rebooting:
|
|
Alternatively, restart the networking service:
|
|
Finally, reboot the device to ensure all configurations are properly loaded:
|
|
Verify the configuration is working:
|
|
VPN Setup
For remote access, I chose Twingate for its excellent free tier, which perfectly suited my needs. Since I had never used it before, I decided to try it for this project. Alternatives like OpenZiti and Tailscale also offer great solutions, but Twingate stood out for its simplicity and ease of setup.
- Created a Twingate account
- Created a new Network (Network > Remote Networks > + Remote Network - select “other”)
- Added a Connector (Network > “network name” > + Add Connector)
- Installed the Connector on my Luckfox Pico (“Inside Connector” > Linux > Generate Tokens > Copy Command)
- SSH’d into the Luckfox Pico and run:
|
|
Twingate Client Setup (Optional)
If you want to use the device as a client as well, install the Twingate client:
|
|
Resources Configuration
I added resources through the Twingate dashboard (Network > Resources > + Resource)
Automatically Adding Resources
To make the device truly plug-and-play, I created a Python script that automatically discovers and adds network resources via the Twingate API. This eliminates the need to manually configure resources for each new network.
1. Install Python dependencies:
|
|
2. Settings > API > Generate Token
3. Replace the variables in the script accordingly.
|
|
3. Running at Startup
To run the script at startup, I added the following entry to crontab:
|
|
If necessary, adjust the file and log paths accordingly.
4. Testing
To verify that everything is working correctly, I simply restart the device and check if new resources have been created in Twingate. I then log in to the Twingate website to confirm the new resources.
In my case, three new resources were created:
- LAN network IP (connected to the AP): 172.16.0.91
- USB connection IP: 172.32.0.70
- Public IP: xxx.xxx.xxx.xxx
5. Resource Permissions
With these resources added, I can grant access to either everyone or specific groups. In my case, I assigned the resource to “Everybody.”
To verify permissions, I use the Twingate CLI on my host machine:
|
|
6. TCP and UDP Port Permissions
It is also possible to allow or restrict specific ports for each resource. By default, all ports are open (*).
7. Testing the Connection
Once outside the network, I can test the connection by running:
|
|
This establishes a remote connection to the device.
Testing the Setup
I started by adding SSH access to my Luckfox Pico as a resource. Then, I scanned my network for potential targets:
|
|
Once I identified available ports, I manually added specific resources to Twingate. For example, if I found a device at 172.16.0.80 with port 80 open, I could add it as a resource. After that, I could access the device through my browser as if I were inside the network.
Troubleshooting
Here are some common issues I encountered and their solutions:
Network Interface Issues
Problem: eth0 interface not coming up automatically
|
|
Problem: DHCP not working
|
|
Twingate Connection Issues
Problem: Connector not connecting
|
|
Problem: Resources not accessible
- Verify resource permissions in Twingate dashboard
- Check if ports are correctly configured
- Test connectivity:
telnet <resource-ip> <port>
Python Script Issues
Problem: API script failing
|
|
3D Printed Case
To protect my device and make it more portable, I looked into printing a case. Here are the models I found most useful:

Performance & Limitations
Network Performance:
- Ethernet: 100Mbps (Fast Ethernet)
- Typical throughput: 80-90Mbps
- Latency: +20-50ms (depending on VPN service)
Power Consumption:
- Idle: ~1.5W
- Active: ~2.5W
- Can run on power banks for 8-12 hours
Limitations:
- No PoE support (requires separate power)
- 100Mbps max speed (no Gigabit)
- Limited to 256MB RAM
- Depends on third-party VPN service reliability
How to Use?
It’s super simple! I just plug the hardware into the Ethernet port, power it with a power bank, a DC adapter, or whatever nearby USB port happens to offer 5V and voilà!

Future Improvements
Here’s what I’m planning to add to my project:
- ESP32 integration (ESP-Hosted)
- Battery installation
- RTC implementation
- Penetration testing scripts
- Custom OS with ESP32, security tools, and testing scripts
