Ethical Hacker
Offensive Cyber Security
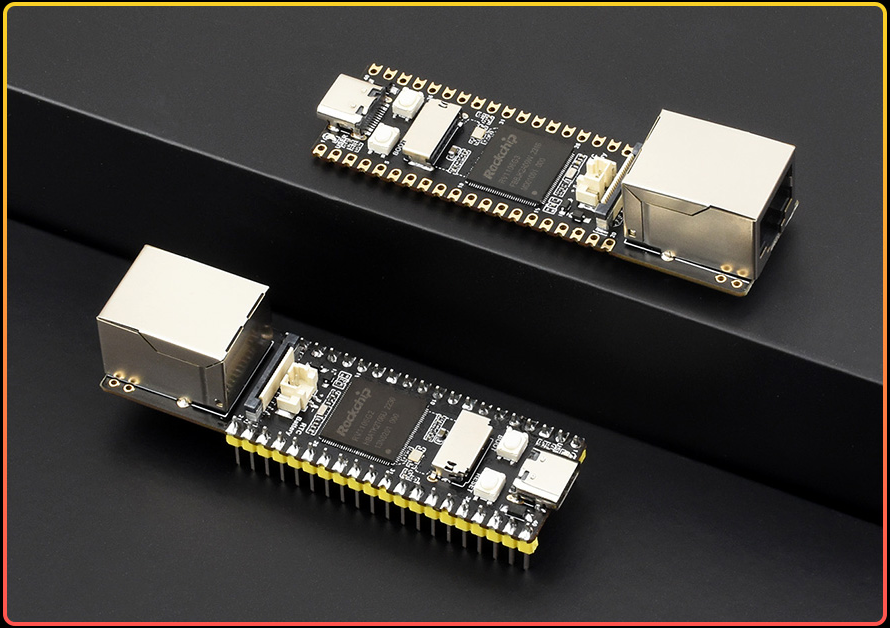
In this post, I share my experience building a DIY stealth remote access device using the Luckfox Pico Max RV1106. Inspired by the commercial LAN Turtle but seeking a more affordable solution, I created this device to enable remote network access without complex port forwarding or traditional VPN setups. This project served as both a practical solution and a valuable learning experience in hardware integration and network security.
⚠️ WARNING ⚠️ This project uses free third-party services!
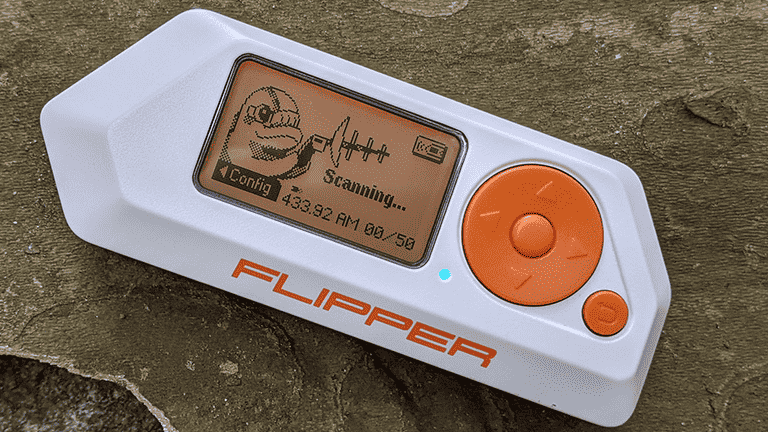
I recently acquired a Flipper Zero, a multi-tool device that can be used for a variety of tasks, including security research, hardware hacking, and DIY electronics. In this blog post, I will share my first impressions of the Flipper Zero, as well as some of the projects I have been working on with it.
I am excited to explore all of the possibilities that the Flipper Zero has to offer. I believe that it is a valuable tool for anyone who is interested in security, hardware, or electronics.
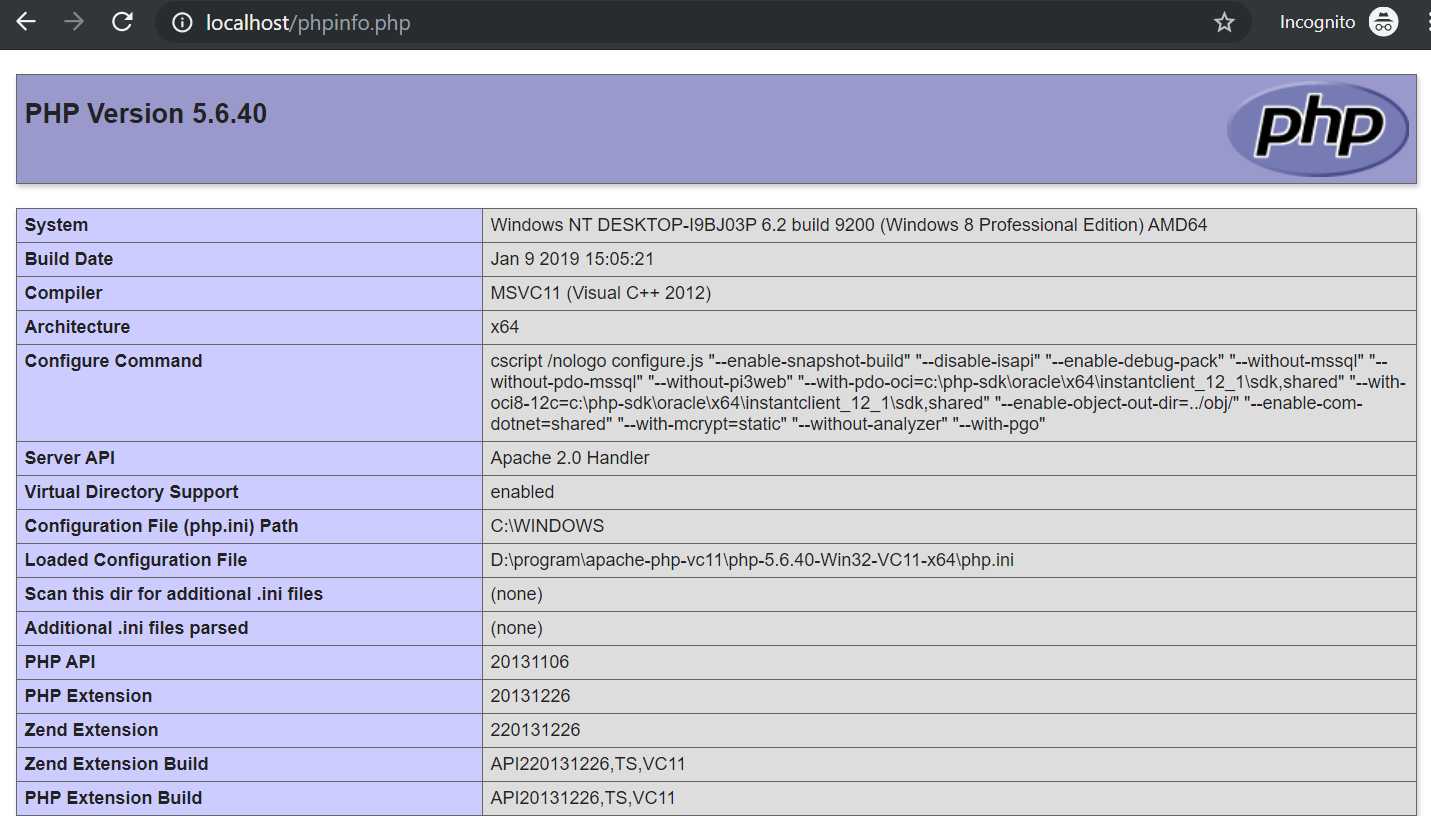
In this instance, I will delve into an LFI (Local File Inclusion) vulnerability and an RCE (Remote Code Execution) vulnerability. I will utilize the tools within the ‘pearcmd.php’ file to craft manipulated files. Within a web environment, we can leverage the functionalities of ‘pearcmd’ by controlling command-line parameters. This Proof of Concept (PoC) is highly specialized, yet it serves as an opportunity for me to explore new methods of penetration within web environments.
This article is about a phishing campaign that my company received. The campaign targeted Saphety, a Portuguese company providing electronic invoicing services. When my enterprise received the phishing email, I decided to investigate further. In this article, I will share my findings.
Summary Summary What is Saphety? The phishing email Website analysis Decoding the encoded strings Form analysis POST method analysis Server analysis What is Saphety? Saphety is a Portuguese company that offers electronic invoicing services.
Since I started my journey in the world of cybersecurity, I’ve been learning and improving my skills in this area. I’ve been asked a lot of times about the resources I used to learn ethical hacking, so I decided to create this post to share with you the resources I used to learn ethical hacking.
Summary Summary How to start? Where to learn? CTFs Blogs Github repositories Tools Being up to date How to start?